Research Interests
"Dependability meets Data Analytics, and at Large Scales"
The above sums up our current research direction. We work on software systems to enable them to perform their functionality in the face of natural and malicious failures. We apply and adapt data analytic techniques to work with the noise of computer
systems and at large system scales. This involves adapting and extending results from learning theory in the domains of adversarial ML and computer vision.
The broad goal of our research is to design practical dependable and secure distributed systems. This finds expression in various domains, which currently include, cloud and edge systems, embedded “bare metal” systems, networks of interdependent assets from multiple ownership domains, cellular and wireless systems, and secure enterprise systems.
For details of my research projects, take a look at the home page of the Dependable Computing Systems Lab (DCSL), its Projects page, and the Research Overview document.
Hot links:
- Google Scholar
- Research overview
- Research impact
- Dependable Computing Systems Lab (DCSL)
- Publications
- Ten most significant publications
- Army Research Lab Assured Autonomy Innovation Institute (A2I2)
- DSN Hall of Fame
- Professional service
- Videos
A sample of our current projects
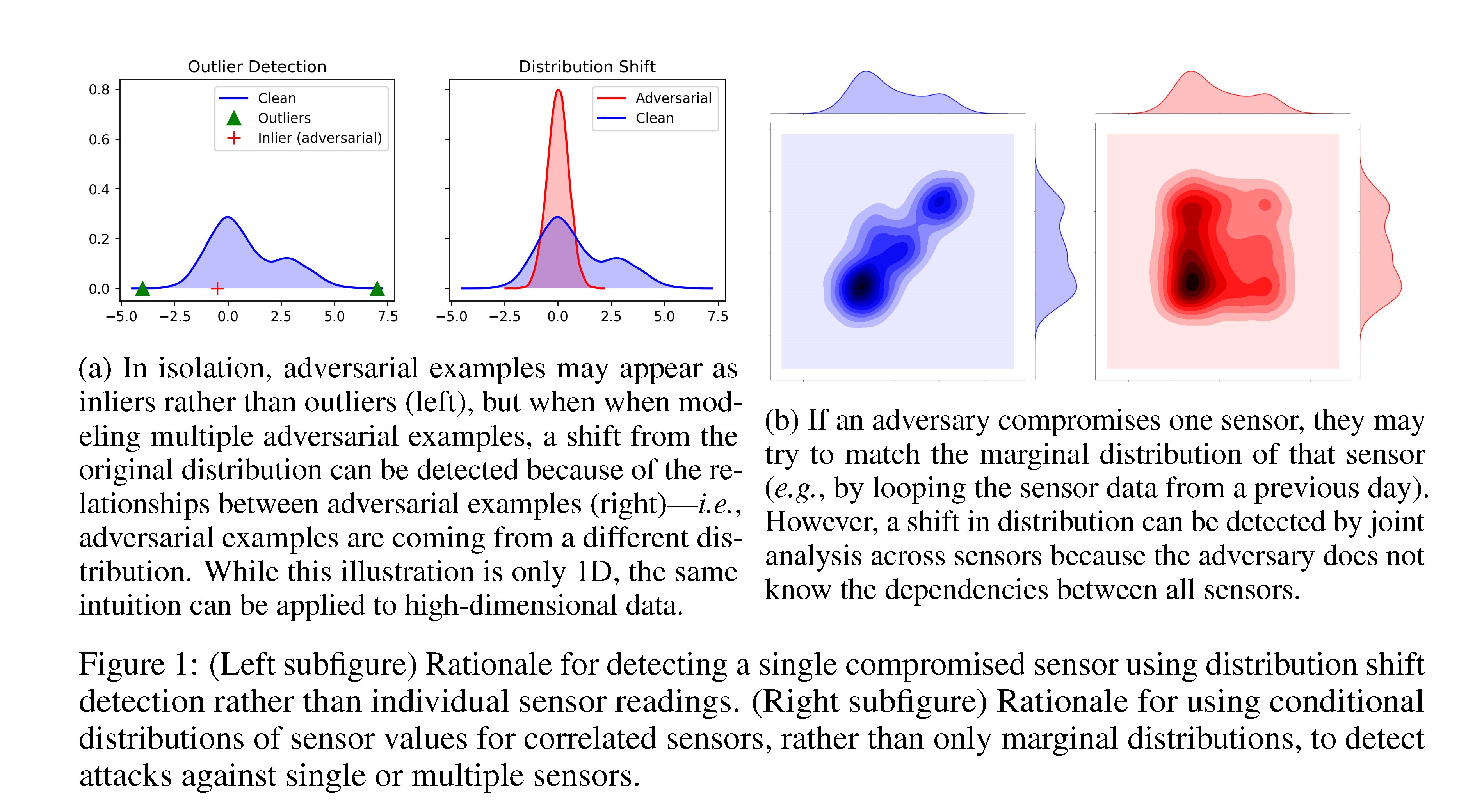
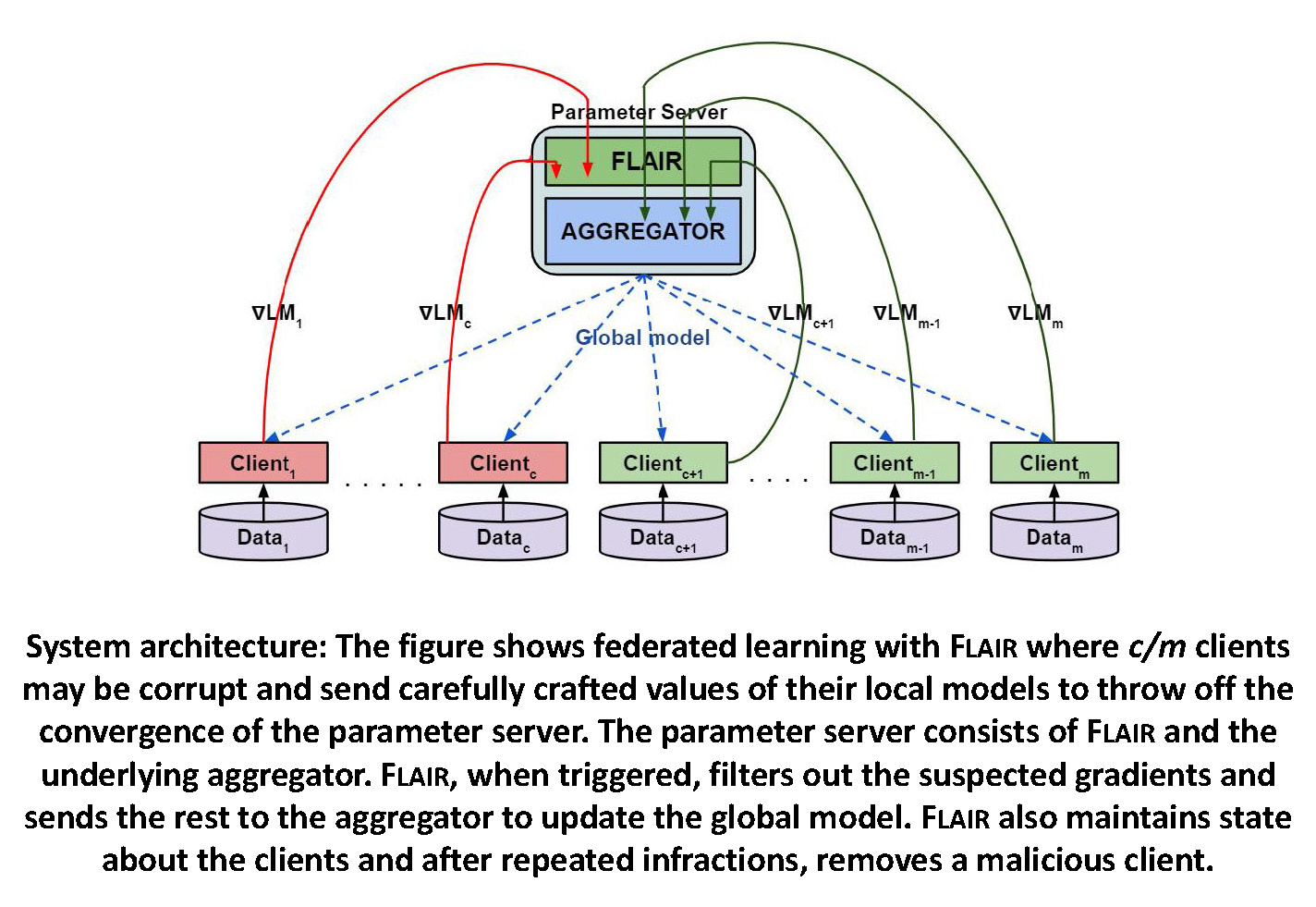
Security of distributed machine learning & Machine learning for distributed system security
How can distributed machine learning be secured by careful adaptation of techniques from applied crypto and distributed computing, adapted to deal with nuances like how optimizations behave in a group? The complementary question is can machine learning be used for securing distributed systems? Our focus is on embedded systems of resource-constrained wirelessly connected nodes.
Further reading: AIStats-22, AsiaCCS-21, NeurIPS-20
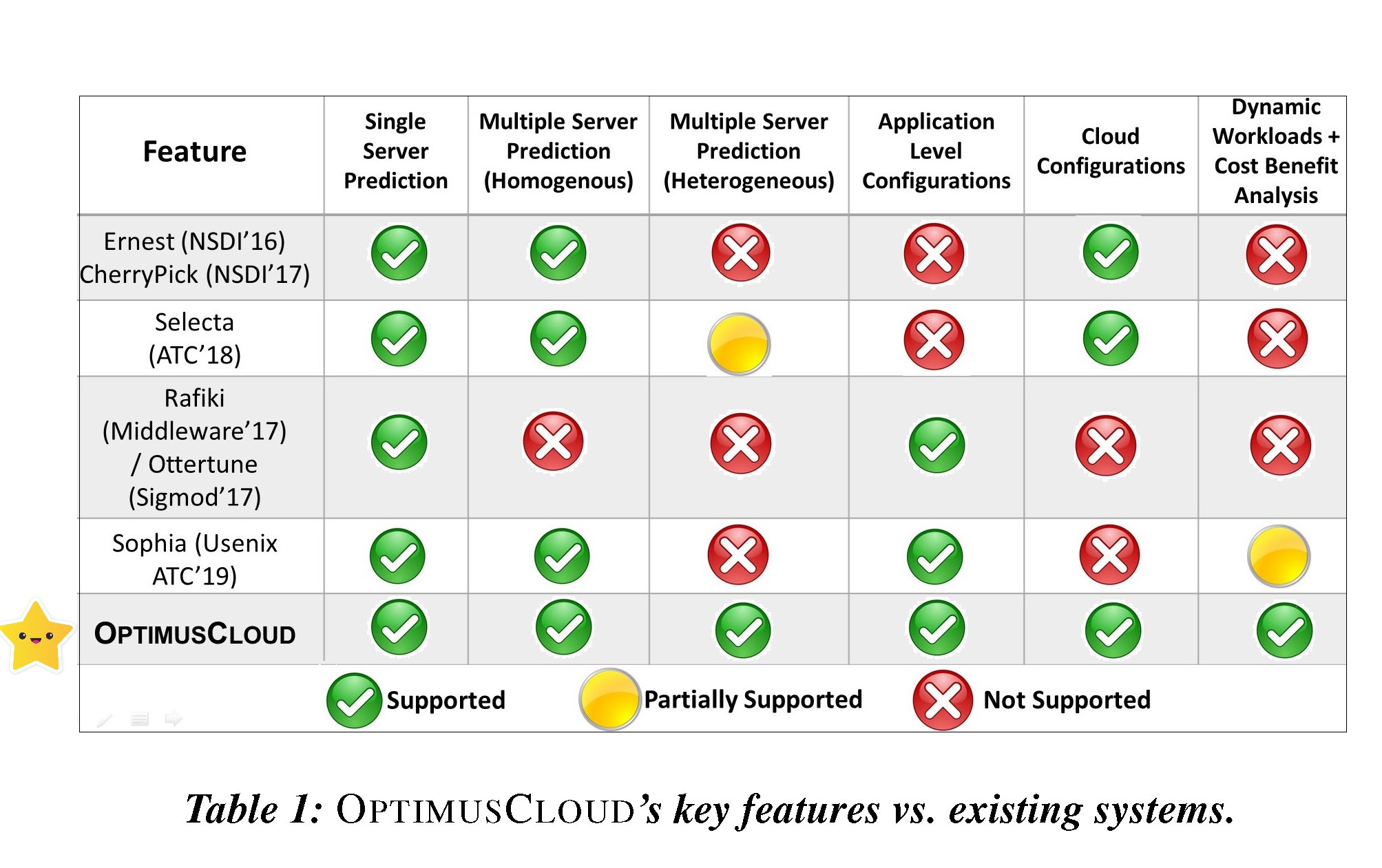
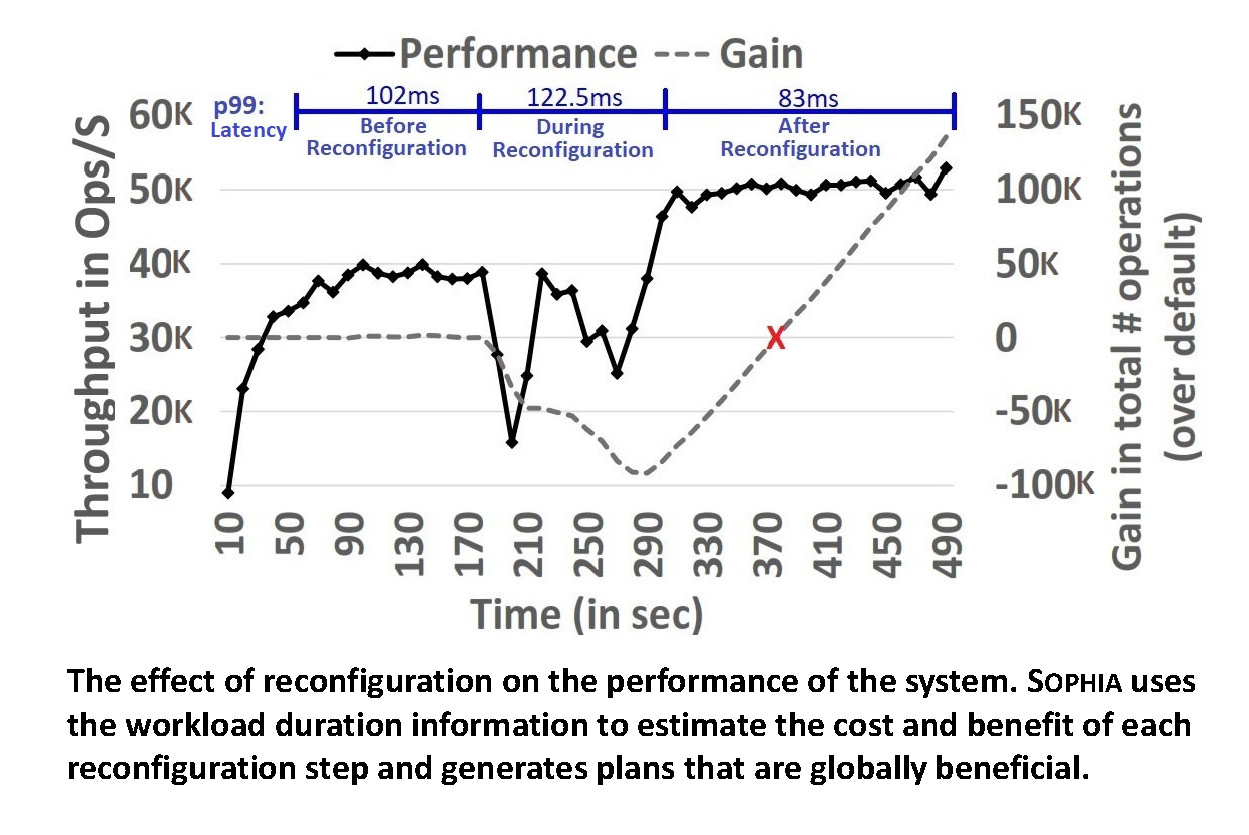
Online reconfiguration of stateful distributed applications
Distributed systems are all around us, providing the backbone of the computing infrastructure that we rely upon --- think of the mesh of computing nodes connected by wireless and wireline networks of various kinds. The question we are answering in this project is: Can these distributed systems stay available continuously as well as reconfigure when things change, say when the workload changes or the user requirements change? This is particularly challenging when the systems carry large amounts of state, such as, NoSQL databases.
Further reading: OSDI-22, Sigmetrics-22, UsenixATC-20
Embedded and wearable security
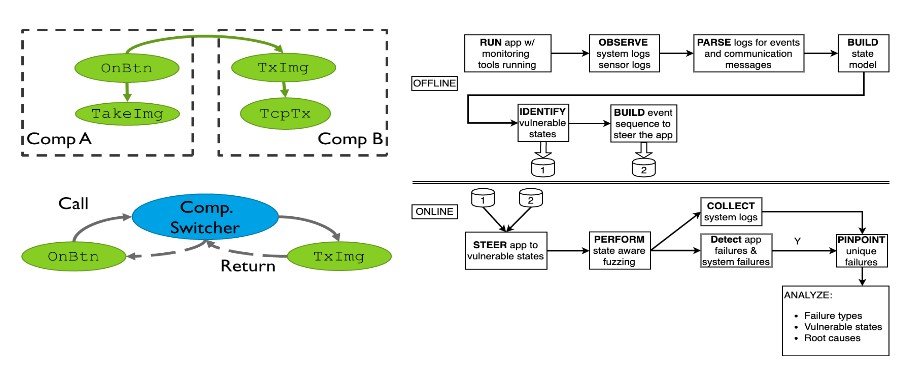
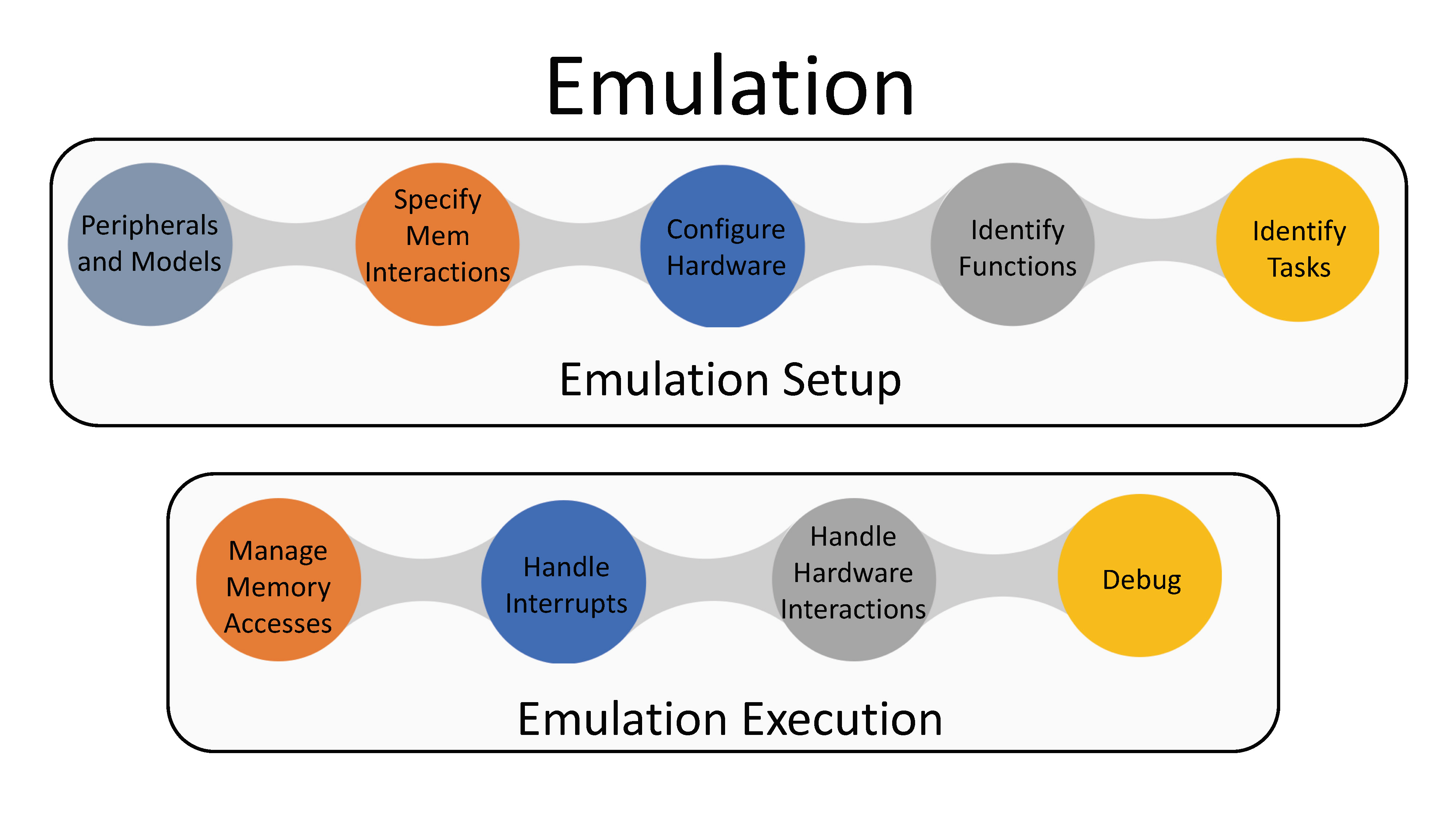
With more than 9 billion embedded processors in use today, the number of embedded devices has surpassed the number of humans. The increasing network connectivity coupled with the ubiquity of these devices makes securing IoT systems a critical task. Our approach shows how to do compartmentalization of individual devices, re-hosting for analyzing their firmware, and distributed protocols like secure state machines for networks of such devices. We are also discovering novel vulnerabilities in wearable devices and showing architectural changes needed to fix them.
Further reading: S&P-22, NDSS-20, UsenixSec-20
Streaming analytics with guarantees
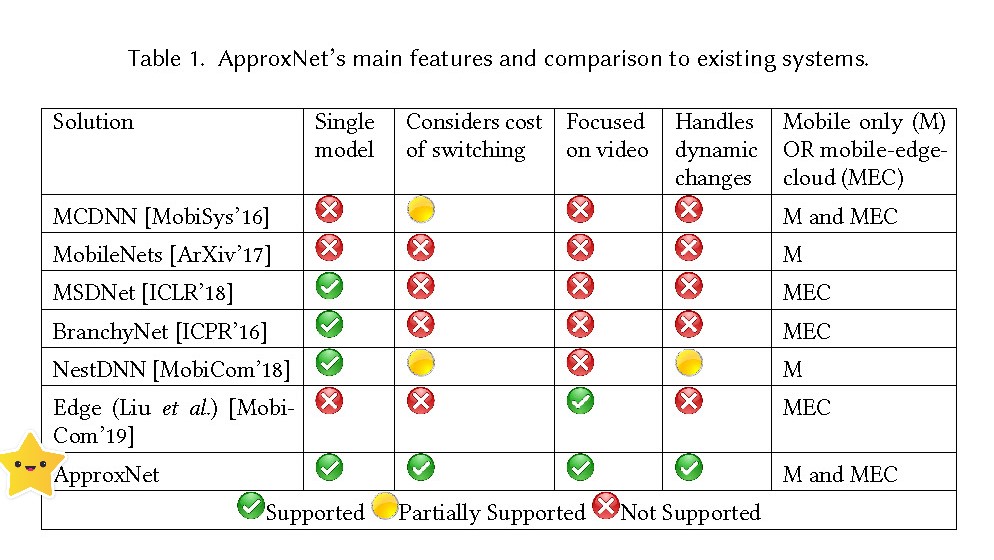
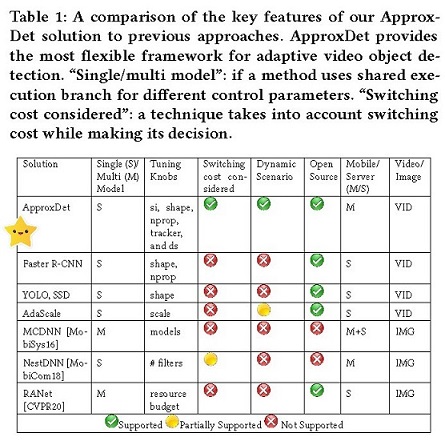
Many computations are inherently approximate---they trade off quality of results for lower execution time or lower energy. While the current approximate computing approaches show that the techniques have a lot of promise, making robust predictions about accuracy and latency is a key challenge to successful adoption of approximate computing in real-world applications. Our work is developing core principles for approximate computing techniques to real-world applications running on sensor and edge computing platforms. Our focus is on streaming analytics such as on sensor or video streams.
Further reading: CVPR-22, EuroSys-22, Sensys-20, TOSN-20
Funding sources
 National Science Foundation (CPS, SaTC, CCRI, SPX) |
 National Institutes of Health (NIAID) |
 Department of Energy (Sandia, Argonne) |
 Department of Defense (Army Research Lab) |
 Eli Lilly |
 Northrop Grumman |
 (Faculty Research Award) |
 Adobe Research |
 Amazon Web Service (AWS) |
Past funding has also come from the Missile Defense Agency (MDA), Indiana 21st Century Research and Technology Fund, private organizations (AT&T Labs, GE Research, IBM, Lockheed Martin, Avaya, Tellabs, Motorola, Intel), and Purdue Research Foundation.
If you are interested in working in the research group, please take a look at the process for this outlined here.